Access Control Software
Managing access rights and security has never been easier with our Evolution Access Control. Our integrated solution ensures that you remain in control, whether you’re on-site or managing access remotely.
Access Control Hardware
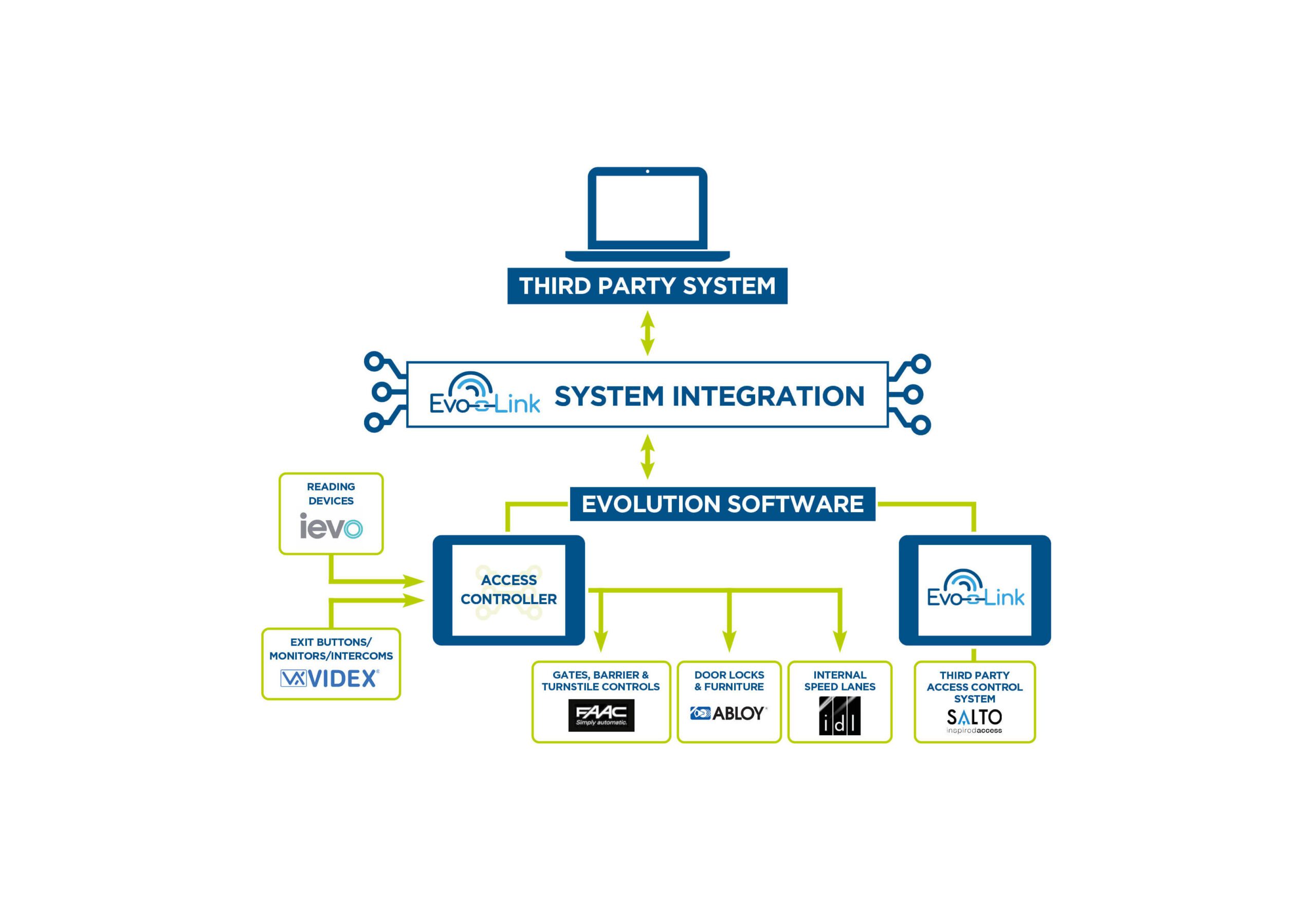
TouchStar’s access control systems integrate seamlessly with various physical security solutions, including turnstiles, biometric readers, and intercoms. We partner with leading hardware providers like IEVO, Salto, and Abloy.
Hidden Access Control Systems
For a discreet approach to access control, consider our hidden access control technology. It includes PIR sensors, door detectors, speed gates, door pass-through systems, and access to CCTV analytics.
TouchStar System Integration
Our EvoLink system integration tool offers flexibility, scalability, and reliability. It facilitates data sourcing and processing from both core and third-party systems to seamlessly streamline your operations.
In today’s rapidly evolving world, securing your business premises and assets has never been more critical. TouchStar’s Access Control Systems offer an end-to-end solution to meet all these security needs and more.
Our modular access control systems offers flexibility and scalability, making it suitable for both single-site and multi-site facilities. Whether you’re a small business or a large organisation, we offer cost-effective solutions that can adapt to your needs.
Benefits of TouchStar Access Control Systems:
Prevents Theft and Loss: Our access control systems extend security and audit trail information throughout your organisation, reducing the risk of theft and loss.
Improves Administrative Efficiency: Streamline your operations by exporting data directly to other business systems, eliminating manual entry and potential data errors.
Enhances Operational Efficiency: Integrate reliable and secure technology for the smooth flow of people within your premises, improving overall efficiency.
Provides Flexible and Remote Administration: Empower yourself with the ability to control access from anywhere, using network-connected devices like PCs and mobile applications.

Our NSI Gold approved, UK-based engineer provide IT consultancy, software and support services provide an end-to-end IT service you can rely on.
IT Consultancy / System Integration
Our expert IT consultancy and system integration services help businesses implement, optimise, and future-proof their critical systems and deliver enhanced efficiency and compliance.
Business Application Software
Our business application software enhances operational efficiency using scalable, configurable solutions that integrate seamlessly with existing infrastructure and systems.
Support and Maintenance Services
Our comprehensive support and maintenance services ensure your critical systems perform reliably and securely. Our experts provide responsive support for all your workforce management needs.
Alongside our core access control systems, we provide a range of peripherals and accessories, including smart ID card printers, lanyards, and badge holders. These additional elements enhance your access control experience.

With an array of options available, finding a solution that aligns with your specific business objectives can be challenging. At TouchStar, our extensive experience in access control systems has enabled us to create this buyer’s guide to help you confidently select or upgrade a access control solution.


Access Control
CCTV
Intruder Security
What do NSI and NACOSS Credentials Mean?
Here, we take an in-depth look at the NSI and NACOSS standards, what these mean and why busine...

Access Control
Fire Security
Time and Attendance
Why Every Business Needs a Commercial Intruder Alarm System
In this blog we look at Automatic Facial Recognition (AFR) and whether it is an effective step...

Access Control
Fire Security
How Does Biometric Access Control Work
Learn how biometric access control uses unique traits like fingerprints and facial scans to pr...

Access Control
Fire Security
What To Look For In An Access Control System
Access control systems are crucial in today’s security landscape to identify, authorise,...
Get in touch for a no obligation conversation about your current situation, needs and challenges and we’ll provide you with the ideas and solutions that will change how you do business for the better.